A recent lab build showed me that in spite Microsoft’s evangelism for Powershell scripting, every product is not yet aligned and also made me discover a nice Powershell Module about PKI management.
The initial goal of my lab was to test the Active Directory Federation Services role from the Windows 2012 R2 release. As the wizard requests you to have a certificate, I genuinely told myself I can use this new New-SelfSignedCertificate introduced in the very same OS.
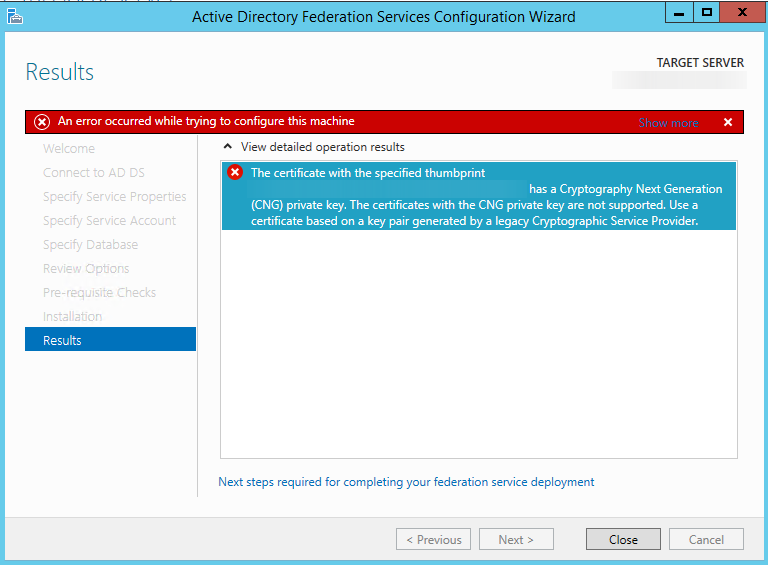
Unfortunately after a couple of pages, the AD FS wizard yells at you with such a message:
The certificate with the specified thumbprint XXXX has a Cryptography Next Generation (CNG) private key. The certificates with the CNG private key are not supported. Use a certificate based on a key pair generated by a legacy Cryptographic Service Provider.
Many web pages will tell you to manually craft a request from your CA, Certification Authority, and have it signed by a “simple” provider. Fortunately, there’s an easier method: just find a way to have a self signed certificate signed also with a simple provider. The Microsoft provided cmdlet however does not allow you to specify such option when called.
You have to call at the community and you may well be heard by installing the PS PKI module at Codeplex. There’s a function called New-SelfSignedCertificateEx which allows to fill your request with the needed options. As far as our AD FS 3.0 requirements are concerned, the following command will do the trick:
<pre class="lang:ps decode:true " title="ADFS 3.0 Compatible Self-Signed Certificate">New-SelfSignedCertificateEx -Subject 'CN=yourfederationname.yourdomain.com' -ProviderName "Microsoft Enhanced RSA and AES Cryptographic Provider" -KeyLength 2048 -FriendlyName 'OAFED SelfSigned' -SignatureAlgorithm sha256 -EKU "Server Authentication", "Client authentication" -KeyUsage "KeyEncipherment, DigitalSignature" -Exportable -StoreLocation "LocalMachine"