Often sought on the Internet, rarely complete, here is for member server firewall ports to open for your Windows domain-joined or soon-to-be-joined machine to be able to contact the domain controllers it is depending on:
- UDP/123 for time synchronization, as in a domain by default the W32Time of a member server synchronizes with the Domain Controllers
- TCP/464 and UDP/464 for joining and regularly changing the computer account password
- TCP/445 for SMB communication (forget about 137, 138, they are unnecessary since Windows 2000!)
- TCP/88 and UDP/88 for Kerberos communication (although you can force Kerberos to use TCP if you wish)
- TCP and UDP/53 for DNS resolution
- TCP/389 and UDP/389 for LDAP
- TCP/636 if you are using LDAPS
- TCP/3268 for joining the domain controllers as global catalog
- TCP/3269 for joining the domain controllers as global catalog over SSL/TLS
- TCP/135 for the RPC endpoint mapper
- a range of ports, by default, 49152-65535 for RPC dynamic ports; you can (and should) limit them so the RPC ports use a narrower range of ports. The number of ports depend on the workload of the machine. Thousand ports is more than OK in most scenarios.
As a bonus for this post, here is a nice poster for you to dream about that: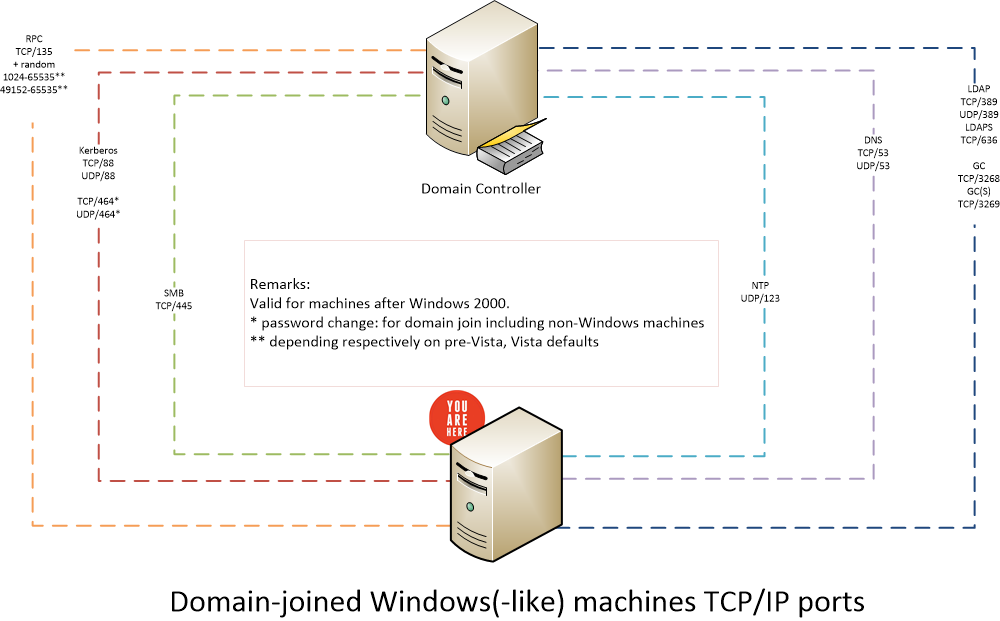 In addition to the member server firewall ports, you may need the domain controller firewall ports list
In addition to the member server firewall ports, you may need the domain controller firewall ports list